ISP Redundancy with SonicWall
If you have used the internet then you know that there will be disruptions and that many of those disruptions are caused by your ISP.
The best part is that you can minimize ISP caused internet disruptions by having multiple ISPs and configuring your router/firewall to failover properly when one link has a failure. The SonicWall firewalls have built in support to manage multiple ISPs with failover. While this article was created using a SonicWall TZ 215 running SonicOS Enhanced 5.8.1.13-1o, the steps are pretty much the exact same using other SonicWall models and SonicOS versions, such as my NSA 3500 running SonicOS Enhanced 5.9.0.3-117o. Everything is pretty much the same. Differences will be seen in the number of interfaces. This article will explain configuring multiple ISPs/WANs on SonicWall firewalls.
Inbound vs Outbound Link Balancing
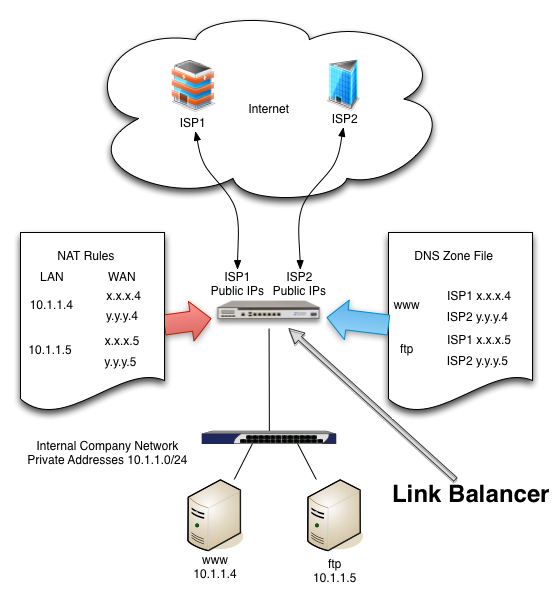
The important thing to understand is the difference between inbound and outbound ISP redundancy. If you have servers on the inside of your network that need to be accessed from outside, you will want to have inbound redundancy. You may wish to read a previous article on Link Balancers that explains how this can be done. However, if what you need is just outbound link balancing, then your SonicWall should be able to do exactly what you need. Even better, this article will show you how!
Configure Your SonicWall for Multiple ISPs/WANs
Step 1 – Physical Connection
Your SonicWall will typically have multiple interfaces that can be used for ISP connections. In the image above the typical LAN(X0) and WAN(X1) interfaces are likely already being used for your first ISP/WAN and your LAN. For this example, I used interface X2 for my second ISP. If it is available, then plug your second ISP’s uplink cable there.
Step 2 – Configure Your X2 Network Interface
Next, we need to login to the SonicWall Firewall with your web browser. Navigate to Network / Interfaces. Find X2 in the list and click on the pencil edit button for X2.
First, you will want to set the Zone for this interface to “WAN”.
Next, you will type in the static or DHCP IP Addressing information that your ISP gave you.
If you want to be able to manage your SonicWall using this address and interface, then allow that by checking the protocols on the Management Line.
Click Ok, when done.
Step 3 – Browse to Network / Failover & LB
Enable load balancing by checking the “Enable Load Balancing” check box, then under “Groups”, find the “Default LB Group” and click the Configure / Pencil button for the Default LB Group.
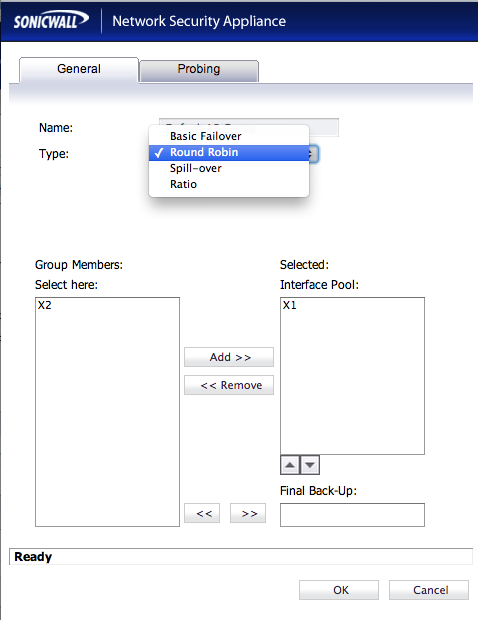
At this point, you will need to choose a “Type” for this Load Balancer. There are 4 types to choose from:
* Basic Failover – Probes the internet on both interfaces, but all traffic goes through your primary. If the primary goes down, traffic goes through secondary.
* Round Robin – Traffic goes equally over both ISP interfaces. If one goes down, all traffic goes through the one that is still up.
* Spill-over – All traffic up to a specified MBPS rating goes through the primary ISP interface, traffic over the threshold goes through the secondary ISP interface.
* Ratio – When both ISP interfaces are up, traffic goes through each using a specified ratio that we configure adding up to 100% (70-30,60-40,etc…).
Make your “Type” choice. I chose “round robin” which makes the options you see above. I then chose the X2 interface and added it to the Selected Interface Pool on the right using the “Add >>” button. Your options will be slightly different depending on the “type” choice you chose above. For Spill-over, you will choose how much bandwidth to use on the primary before spilling traffic over to the secondary interface. If you chose ratio, you will decide what percentage of the total traffic to send over each interface.
Configure Probing
Probing is what is used to detect if an ISP is up and operational or not. We tell it how frequently to check the interface, how many failures it takes to deactivate the interface, and how many successful checks to make before reactivating the interface again.
We also can check the “Probe responder.global.sonicwall.com on all interfaces in this group” to have it probe the SonicWall system through each interface for the probe. Set these the way you want and then…
Click Ok. This will bring you back to the Failover and LB page.
You should see something similar to what is shown in the image above with both interfaces in the group and statistics displaying. Be sure to click the “Accept” button.
Your SonicWall should now be configured for Failover and Load Balancing.
Latest posts by Jeff Staten (see all)
- Configure Your HP Procurve Switch with SNTP - May 5, 2015
- Configuring HP Procurve 2920 Switches - May 1, 2015
- Troubleshooting Sendmail - November 28, 2014





I dont want to use load balance or etc – I want X1 and X2 to be mutually exclusive.
How do I make something that came IN on X2 go OUT X2 instead of X1 – which is the default route out?
Thanks in advance !!.
D
mrmann1234,
Not understanding fully your configuration, I would imagine that the way to handle this would be using NAT policies properly. If NAT is specific to certain host’s private addresses, and those host’s are not multi-homed nor multi-NATted, then the traffic should exit X1 if it came in X1 because of the public address accessed and used through NAT.
Both X1 and X2 are WAN ports
X1 = ISP1
X2 = ISP2
Different IP scope on each.
Right now – the OWA access rule is set to use “Wan IP” – So both X1 and X2 will route to OWA – but when OWA sends back OUT – it is using X1 – even if the request came in on X2.
If something comes in from X2 – say – a client to an OWA server – I want the response OWA sends to go OUT X2. Currently it leaves from X1.
I hope that makes more sense?
Thanks!
Mrmann1234,
I guess what I am trying to say is that I believe the only way you can resolve this is by directly NATting the specific machines with their own public address in the SonicWall NSA with an address from the ISP that you want them to respond with. I believe that is the only way to guarantee it will respond through the proper interface and thereby ISP connection.
Jeff ,
We are in the process of adding a new WAN line for redundancy? Since Wan 1 are natting and are associated with the public dns. If we were to add Wan 2 for load balancing, how would the internal natting works going out to Wan2
Andy,
Are you worried about setting up a 1 to 1 NAT for an internal server with an external presence? Or are you just referring to the default 1 to many NAT for all workstations on the inside?
If it is the 1 to many, all workstations will be NATted to the WAN’s interface that the traffic passed out.
If it is a 1 to 1 NAT, it will follow the priority of the NAT rules in the Network / NAT Policies.
We have many website hosting, a owa for email, and a couple of others. Lets say currently we have only ISP on Sonicwall. if we add a new WAN ISP, do we have to nat the internal ip to the new WAN and have a secondary DNS so that it know?
For instance, with our current source 172.50.240.5 (internal) got translated to 174.50.64.10. Now if you add a new WAN ISP, how would 172.50.240.5 know if it’s going to 174.50.64.10. Doesn’t the new WAN ISP has a different ip’s from a different company?
Andy,
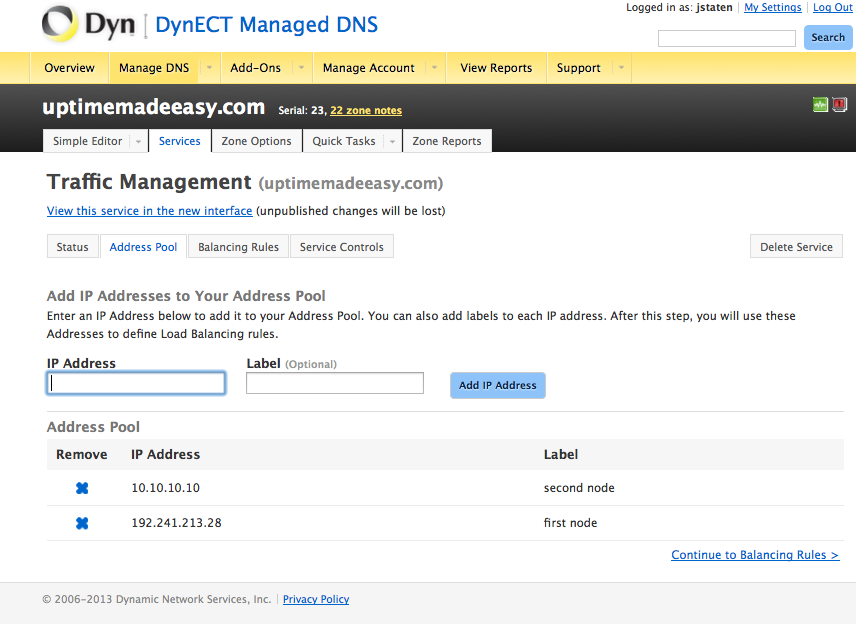
If you are dealing with internal machines that need an external presence, then to use the SonicWall for ISP failover, you will have to NAT both addresses, each to an address from each ISP. However, you are going to have to use some sort of DNS scheme to manage the DNS so traffic is routed only to your addresses on ISPs that are up. Otherwise, how would you regulate traffic when one of the WANS is down? For example, you could use, Dyn’s failover service, or their traffic management service (see: http://www.uptimemadeeasy.com/networking/setup-dynect-dynamic-dns/ ) or other products from netriplex (see: http://www.netriplex.com/dns-hosting/ )or DNSmadeeasy.com (see: http://www.dnsmadeeasy.com/services/dns-failover-system-monitoring/), otherwise, people browsing for your page will not be able to find your webpages when they are down.
A different alternative is to use a link balancer with a built in authoritative DNS like what I describe in an earlier article (see: http://www.uptimemadeeasy.com/networking/choose-a-link-balancer/). Most link balancers will detect a downed ISP and respond to DNS requests to the ISP’s address that is up only.
Exactly. That’s what I thought initially is to connect the new ISP, add additionaly copy of the existing custom Nat polices with the New ISP. then maybe use one of mentioned services to manage the dns failover. Does that sound about right? Now if we were to use the Link Balance, we do not need a dns failover or to add additional custom nat?
Yes either one of those 2 methods would be the way to go in this case.
How much a Ecessa 250 would cost?
I would suggest contacting the vendors directly for specific pricing information.
With the link balancer, do you take the custom nat policies from the sonicwall and place them all on the Link Balancer? It looks like you still have to address the wan isp 2?
Link balancers by their very definition handle the ISPs/WANs for you just like my article explains.
When I have used them in the past, I have put them in front of my SonicWall and allowed the LB to handle the NAT rather than the SW.
So another word, you will still have to take out all custom natTing from the sonicwall and add it to the LB. I’m assuming you have to do two sets of natTing for the new second ISP? This basically the same thing right. I guess this eliminate having to have a second public dns because the second set is pointed to the same public dns?
When using a link balancer, it will depend a bit on which one you choose (F5, Peplink, Ecessa, …). The Link balancer will handle all NAT, with addresses from each ISP.
If you intend to use the authoritative DNS feature in a Link Balancer, then be certain that the one you choose has that feature as not all do. If you choose one without authoritative DNS, then you will have to opt for a DNS service with monitoring / failover.
If you have to do all the natTing on LB and get DNS services monitor, what’s the different of doing DLB from Sonicwall and get DNS failover services?
That is why I keep mentioning that you will want one with Authoritative DNS.
There is little difference between SW and LB without authoritative DNS.
Hi Jeff.
Your explanation on how to configure a 2nd ISP/WAN connection was very explicit. I thank you for that. However, having followed your directions to the letter, I am unable to get my 2nd WAN connection to work. Under the Default LB heading, it shows “Link Down” & “Target Unavailable.” Yet, if I connect a laptop directly to the modem (and configure the laptop IP accordingly), I can get out to the Internet. Any idea as to what I may have misconfigured? I am using a TZ215.
Steve,
Because failed probing is what causes the Link down and target unavailable result, I wonder if your upstream ISP is blocking the probes. If you disable the checkbox for probing responder.global.sonicwall.com, it should probe the default gateway for each WAN interface. Could you try this to see if it resolves the issue for you?
Jeff
We’re currently setting up our new Sonicwall firewall and I’m rebuilding the configuration of our old firewall on the new hardware.
In order to update, register and test the Sonicwall I wanted to configure a temporary default route which goes over x0(LAN) to our current firewall.
Is this possible?
I have already configured a default route to our old firewall but still the Sonicwall tries to use the WAN interface.
Mxa,
I am not completely certain that I understand what you are attempting to do. But I suspect that the issue you are having is related to having multiple default routes. You can create multiple routes to the same location (ie: default), but they still follow the order of preference. You may need to disable or remove the current default routes that you have configured to your WANs to make this work.
Jeff
Jeff,
Thank you for the article and sharing it. With this LB using Round Robins, I have noticed issues with HTTPS not working correctly and if mail server is with DNS on primary ISP address, when emails goes on the 2nd ISP WAN, there is a problem with NDR or rDNS is working correctly?
Have you noticed that and what have you done to fix it?
Bora
Bora,
These issues are to be expected when using a SonicWall for inbound link balancing. The intent for SonicWall failover WANS is really meant for outbound use only. I would be hesitant to try to self-host services from behind one of them.
I have had much, much better luck using a link balancer for those types of self-hosting options particularly those with a built in authoritatize DNS server. See my article:
for more information.
Perhaps you would be better served renting VPS space for these services.
Jeff
A Jeff a question! I have two connections to satellite internet, which have high latency. What choices you recommend me select options Failover & LB? DNS which also have to settle for that case?
Sorry for my English!
Excellent article!
Greetings!
Jeff, excellent article congratulations!
I have two satellite internet connections, which I recommend settings for this type of service they have a super high latency. Are currently configured with load balancing and round robin. But it is very unstable, you consider to be the best settings?
Bernardo,
If an ISP is especially unstable, then it will likely fail the probes from time to time. You can try to change the Probing options to see if that helps. If the second ISP is just as unstable and — perhaps even worse going through the same satellite and susceptible to the same outage causes, then maybe you should rethink your ISP options.
If you have no other options in an ISP, then I suppose, this is the best solution that there is for your difficult scenario.
As for your question about DNS, make sure that you are using a DNS service that is dependent on one of the ISPS. Use a DNS service like google or Opendns for your DNS server which should always be available.
Hopefully, you are not attempting to host any servers with internet availability over your unstable WAN, if that is the case, however, the SonicWall is probably not the right solution for you. You should try a link balancer instead.
Jeff
Jeff,
Thanks. For now it is the only option we have. As you say, I understand that it is best to disable load balancing and FB. We just need the service for sending emails and simple navigation. I configure the public DNS to google.
I excuse me for my English, I do not speak very well…