Nagios Remote Plugins with NRPE
Two weeks ago, we setup Nagios in the article: Monitoring Your Systems with Nagios and last week, we defined Nagios hosts and services in the article: Configure Nagios Hosts and Services. This week, we will extend our Nagios to monitor other machines using remote plugins being called over NRPE. NRPE will be communicating through an SSL connection. Using NRPE gives us lots of flexibility in monitoring the remote host. We can even define and write custom plugins to run. In our example below, we will setup Nagios to monitor our webserver host that we defined last week. Specifically, we will monitor the free space in our root filesystem and also verify that the time on the machine matches the time on our ntp time server.
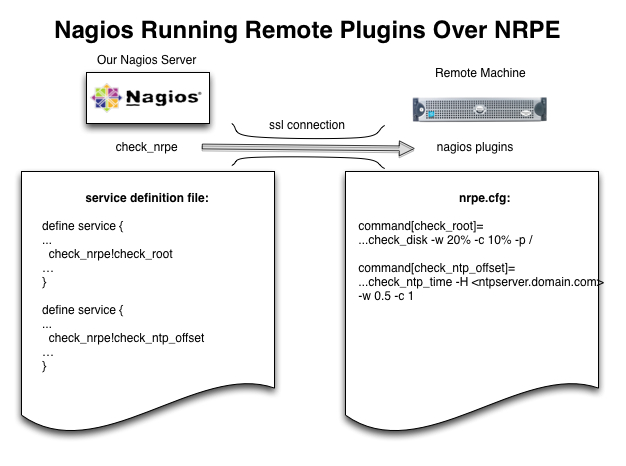
The diagram shows our Nagios server with service definitions for NRPE using the check_nrpe plugin on the nagios server. The check_nrpe plugin is given the name of the remote service definition as a parameter:
check_nrpe!check_root
The check_nrpe plugin will then connect to the remote machine using an SSL connection. NRPE on the remote machine will then invoke the service command defined in the nrpe.cfg file.
Using YUM to Install NRPE and Plugins
There are several tasks that we need to do to get our nrpe connections setup properly. While I will be defining how to download and compile NRPE so that you can install it on any machine or version, CentOS 6 has a repos named: nrpe.x86_64 that you can install with yum. If you use the Yum installation, you will find that your nrpe.cfg file will be found at: /etc/nagios/nrpe.cfg and the plugins will be found at: /usr/lib64/nagios/plugins. If you used Yum to install, skip the compilation steps below. Otherwise, strap on your seat belt, here we go…
Compiling NRPE and Nagios Plugins
1. Install Prerequisites
yum install gcc glibc glibc-common gd gd-devel openssl-devel net-snmp net-snmp-utils make |
2. Download NRPE and Nagios Plugins
| mkdir -p /installs/nagios cd /installs/nagios wget http://sourceforge.net/projects/nagios/files/nrpe-2.x/nrpe-2.15/nrpe-2.15.tar.gz wget https://www.nagios-plugins.org/download/nagios-plugins-1.5.tar.gz |
3. Create the Nagios User
useradd nagiospasswd nagios |
4. Compile and Install the Plugins
gunzip nagios-plugins-1.5.tar.gz tar -xvf nagios-plugins-1.5.tarcd nagios-plugins-1.5./configuremakemake installchown nagios:nagios /usr/local/nagioschown -R nagios:nagios /usr/local/nagios/libexec/ |
With that, the plugins should all be installed!!
Next, we install NRPE.
5. Install Xinetd and Compile NRPE
With CentOS, we run Nagios NRPE under xinetd. We Need to Install xinetd with Yum, Then Compile NRPE.
yum install xinetdcd /installs/nagios/#(do this part if it exists)gunzip nrpe-2.15.tar.gztar -xvf nrpe-2.15.tarcd nrpe-2.15./configuremake allmake install-pluginmake install-daemonmake install-daemon-config
|
6. Edit the /etc/xinetd.d/nrpe File to Allow our Nagios Server to run NRPE Commands
Edit the only_from line to read like this:
|
|
7. Add the NRPE Port to the /etc/services File
cat >> /etc/services <<EOFnrpe 5666/tcp # NRPEEOF |
8. Startup Xinetd
service xinetd restart |
9. Test Our NRPE Connection
Login to the Nagios server and verify that we can run the check_nrpe plugin on the remote host.
/usr/local/nagios/libexec/check_nrpe -H <ipaddress of remote host>NRPE v2.15 |
If it replies back with a version of NRPE as above, then things are good. Otherwise, you probably have a problem with step 6, something isn’t running or there is a firewall issue.
10. Edit the nrpe.cfg File and Verify that the Service Commands are Defined
cd /usr/local/nagios/etc/cp nrpe.cfg nrpe.cfg.origvi /usr/local/nagios/etc/nrpe.cfg |
Edit the custom command area at the bottom and make sure that you have at least these service commands defined below:
|
command[check_ntp_offset]=/usr/local/nagios/libexec/check_ntp_time -H <ipaddress of NTP Server> -w 0.5 -c 1 |
11. Configure the Service Definitions on the Nagios Server
Back on the Nagios server, we need to edit the host configuration file from last week’s configuration and add our check_nrpe commands
use generic-service host_name uptimemadeeasy.com service_description Check Root Filesystem check_command check_nrpe!check_root check_period 24×7 check_interval 5 max_check_attempts 2 normal_check_interval 5 retry_check_interval 1 contact_groups admins notification_interval 15 notification_period 24×7 notification_options w,c,u,r } define service{
use generic-service host_name uptimemadeeasy.com service_description Check NTP Offset check_command check_nrpe!check_ntp_offset check_period 24×7 check_interval 5 max_check_attempts 2 normal_check_interval 5 retry_check_interval 1 contact_groups admins notification_interval 15 notification_period 24×7 notification_options w,c,u,r } |
12. Verify Nagios Configuration
Now that NRPE is compiled, installed, verified, and our service definitions are setup in the Nagios maps, we are ready to verify our configuration.
| /usr/local/nagios/bin/nagios -v /usr/local/nagios/etc/nagios.cfg |
13. Restart Nagios
Now that NRPE is compiled, installed, verified, and our service definitions are setup in the Nagios maps, we are ready to verify our configuration.
| service nagios restart |
Latest posts by Jeff Staten (see all)
- Configure Your HP Procurve Switch with SNTP - May 5, 2015
- Configuring HP Procurve 2920 Switches - May 1, 2015
- Troubleshooting Sendmail - November 28, 2014